Harvard University is committed to protecting the information that is critical to teaching, research, and the University’s many varied activities, our business operation, and the communities we support, including students, faculty, staff members, and the public. These protections may be governed by legal, contractual, or University policy considerations.
Data Security Levels
Harvard Medical School Information Security works with the Harvard Longwood Medical Area IRB and HMS Sponsored Programs in order to review security requirements from Harvard University's Information Security Policy, applicable state and federal regulations, and contractual agreements.
Visit the HMS Information Security website for more details about information security. Questions about HMS information security can be sent to the IT Service Desk.
Research involves increasingly complex arrangements for the storage and transmission of research data. Robust data privacy and security planning is necessary to protect the privacy of research subjects and to secure sensitive, personally identifiable information.
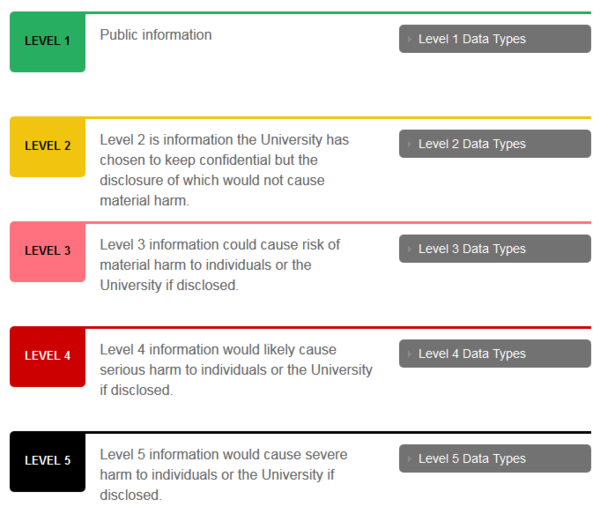
- Review the Research Data Security Levels with Examples to determine your research risk level
- Use the Harvard Catalyst Data Privacy and Security Checklist (PDF) for thinking about your research and prepare an IRB application
-
Data Security Level 3
- Harvard protects confidential data (classified as level 3) with multiple security controls. Any confidential data is required to be encrypted in transit and stored in University-approved systems, such as our institutionally provided Microsoft Office 365, One Drive, SharePoint, Dropbox for business, and network file shares.
- Access to confidential data are granted only to those individuals who have a valid business reason. Access is provisioned using the principle of least privilege. All Harvard University staff are required to take annual information security awareness training.
- Servers that store confidential information are protected by firewalls that limit both inbound and outbound connections. Servers log access and system-level events to a centralized, IT-managed solution. All University systems are required to have Endpoint Detection and Response (EDR) software and Anti-Virus. Systems are required to be kept up to date with the most recent security patches. Local storage of confidential information is permissible on encrypted devices.
- Servers are required to have mechanisms in place to prevent against brute force password attempts. Default passwords are changed before placing systems into production and guest, or generic accounts are disables.
- All individuals are required to choose a unique, strong password. Passwords are prohibited to be shared. In the event that credentials must be shared, an enterprise password vault is used to track and audit access, and to remove access to shared credentials when an individual no longer requires access.
- Administrators are required to use separate accounts for administrative roles and are required to use two-step verification for all administrative functions. Alerts are configured for highly sensitive systems to notify upon administrator logins.
-
Data Security Level 4
- Harvard protects highly confidential information (classified as level 4) with additional security controls. Data classified as level 4 may not be stored on local devices, such as laptops or desktop systems. It may only be stored on servers and services that have been approved to meet additional requirements consistent with level 4 controls.
- Servers are protected by both network and host-based firewalls that are configured to only permit the traffic necessary for the functionality of the system. All traffic between the client and the server is encrypted using modern encryption protocols. Two-step verification is required wherever feasible for end-user access.
- Administrators are required to use separate accounts for administrative roles and are required to use two-step verification for all administrative functions. Alerts are configured for highly sensitive systems to notify upon administrator logins.